Risk management is a critical component of any organization’s strategic planning and operational effectiveness. It involves identifying, assessing, and mitigating risks that could potentially affect the organization’s ability to achieve its objectives. This article provides a detailed overview of the essential elements of risk management, including establishing the context, identifying risks, assessing and evaluating risks, and determining appropriate risk treatment strategies.
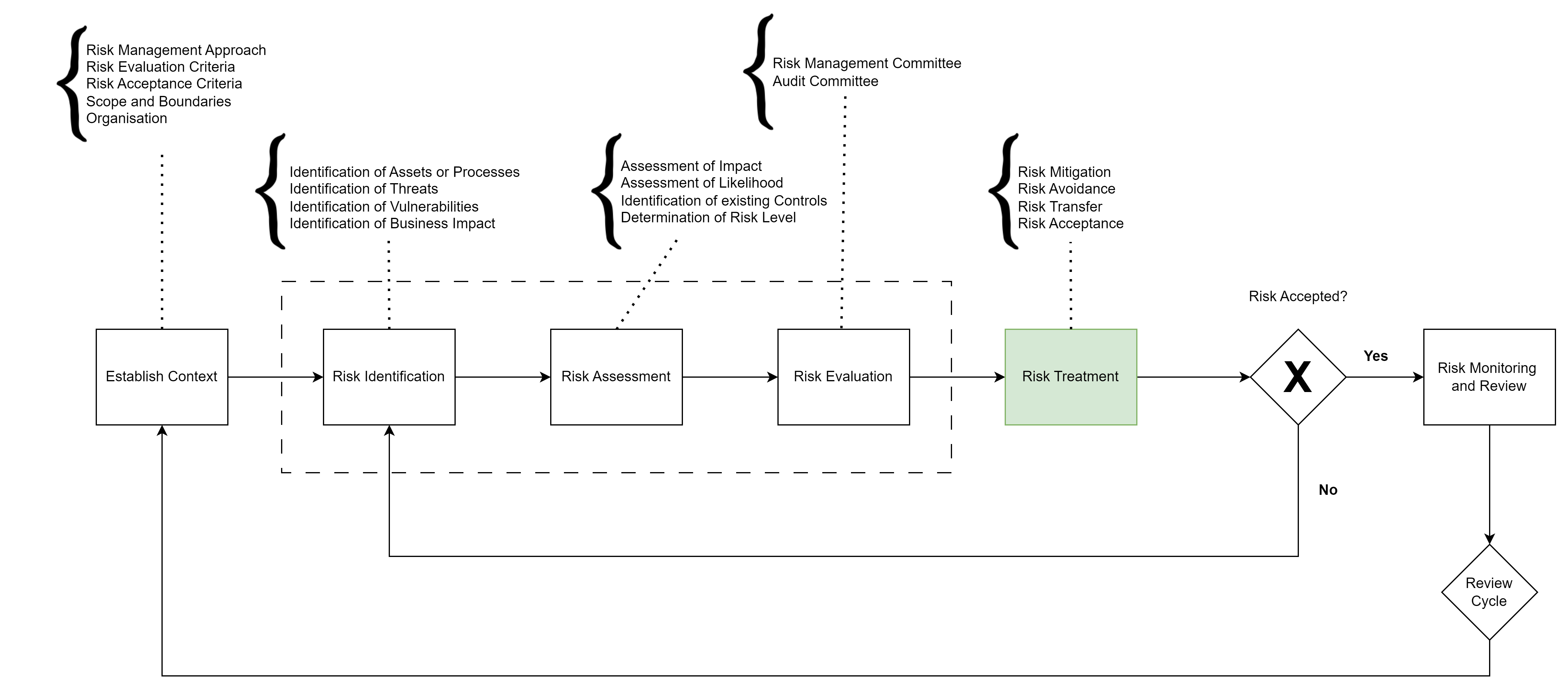
Establishing the Context
The first step in risk management is to establish the context within which the organization operates. This involves defining the approach, evaluation criteria, risk acceptance criteria, scope, and boundaries.
1. Approach: The risk management approach should align with the organization’s overall objectives and strategic goals. It includes the methodologies, frameworks, and tools used for risk management.
2. Evaluation Criteria: These criteria determine how risks will be evaluated, typically based on their likelihood and impact. The criteria should be consistent and transparent to ensure that all risks are assessed uniformly.
3. Risk Acceptance Criteria: This defines the level of risk that the organization is willing to accept without taking further action. It is essential to set these criteria based on the organization’s risk appetite and tolerance.
4. Scope and Boundaries: This involves defining the specific areas, processes, or assets that the risk management process will cover. It ensures that the focus remains on the most critical aspects of the organization.
Risk Identification
Identifying risks involves pinpointing potential threats, vulnerabilities, and the business impact on specific assets or processes. This step is crucial for gaining buy-in from the business as it assigns ownership and accountability.
1. Threat: A threat is anything that can exploit a vulnerability to harm the organization. Examples include cyber attacks, natural disasters, or economic downturns.
2. Vulnerability: A vulnerability is a weakness in the organization that can be exploited by threats. This could be outdated software, lack of employee training, or inadequate physical security.
3. Business Impact: The business impact is the potential consequence of a threat exploiting a vulnerability. It includes financial losses, reputational damage, operational disruptions, and regulatory penalties.
Risk Assessment
Risk assessment involves analyzing the identified risks to determine their likelihood and impact, evaluating existing controls, and calculating the residual risk.
- Likelihood and Impact: Assessing the likelihood of a risk occurring and its potential impact on the organization. This helps prioritize risks based on their severity.
- Existing Controls: Identifying and evaluating the effectiveness of existing controls that mitigate the risks. Effective controls can significantly reduce the likelihood and impact of risks.
- Residual Risk: This is the risk that remains after considering the effectiveness of existing controls. It represents the true level of risk the organization faces.
Risk Evaluation and Treatment
Once risks are assessed, they need to be evaluated and treated appropriately. This involves presenting the findings to a relevant committee that can articulate the risks’ relevance and decide on the appropriate treatment strategy.
Risk Treatment Options:
- Mitigation: Implementing measures to reduce the likelihood or impact of the risk. This could involve enhancing security protocols, updating software, or training employees.
- Avoidance: Eliminating the risk entirely by discontinuing the activity that generates it. This means the risk is not acceptable, and the organization removes the vulnerability.
- Transfer: Transferring the risk to another party, such as through insurance or outsourcing. This does not eliminate the risk but shifts its burden.
- Acceptance: Acknowledging the risk and deciding to accept it without further action, often because the cost of mitigation exceeds the benefit. Accepted risks should be reviewed periodically.
Monitoring and Review
- Accepted Risks: Regularly review accepted risks to ensure they remain within the acceptable level and do not escalate unexpectedly.
- Mitigated Risks: Track progress against the mitigation plans to ensure that actions are effectively reducing the risk.
- Avoided Risks: Ensure that the vulnerabilities leading to the risk are entirely eliminated and that the risk does not re-emerge.
- Transferred Risks: Regularly review the terms of insurance or outsourcing agreements to ensure they continue to cover the risk adequately.
Conclusion
Effective risk management is an ongoing process that helps organizations navigate uncertainties and protect their assets and operations. By establishing the context, identifying risks, assessing and evaluating them, and determining appropriate treatment strategies, organizations can manage risks proactively and strategically. Regular monitoring and review ensure that risk management efforts remain effective and aligned with organizational goals.

Leave a comment